From “Trusted Network Access” to “Verified Every Request”
For many enterprises, VPN has long been the default solution for remote access.
Then, as organizations grew more distributed and cloud-centric, new problems emerged:
- Remote and hybrid work became the norm
- SaaS and cloud applications replaced on-prem systems
- VPN credentials were phished or leaked
- A single compromise led to widespread lateral movement
This is when Zero Trust entered the conversation.
But a common question remains:
Is Zero Trust just a newer version of VPN?
Do we still need VPN at all?
This article explains—from an enterprise, real-world perspective—the fundamental differences between Zero Trust and VPN, when each is appropriate, and why they solve different problems.
1. The Short Answer (For Busy Readers)
VPN answers “How do I get into the network?”
Zero Trust answers “Am I allowed to do this specific thing?”
They are built on entirely different trust models.
2. The Core Design Philosophy of VPN
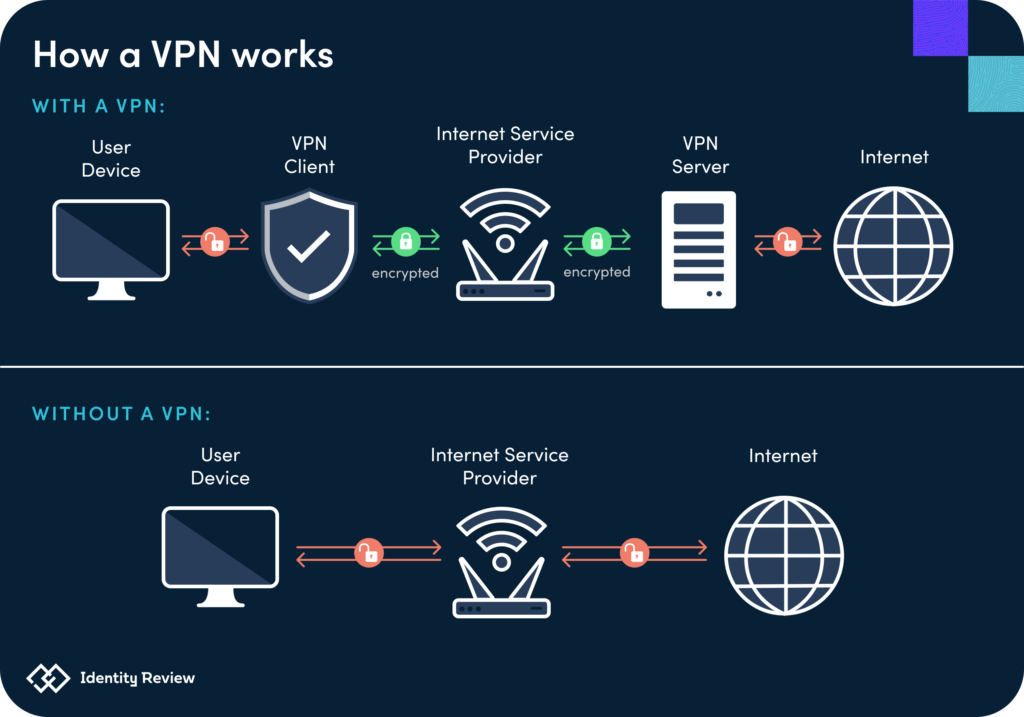
Traditional VPN Access Model
User
│ VPN Authentication
▼
Internal Network
│
▼
Internal Systems
The VPN model assumes:
Once you are inside the network, you are trusted.
What VPN Actually Trusts
- User credentials
- Device access
- Network location (IP, subnet)
Once the tunnel is established:
- The user is “inside”
- Many internal systems become reachable by default
👉 Trust is granted broadly and all at once.
3. Structural Problems of VPN in Modern Enterprises
1️⃣ One-Time Authentication, Permanent Trust
- Authentication happens once
- Subsequent access is rarely re-verified
👉 Trust is static, not continuous.
2️⃣ High Risk of Lateral Movement
- One infected laptop
- One leaked VPN credential
- Attackers can scan and move freely inside the network
👉 VPN often becomes the starting point for internal breaches.
3️⃣ Poor Fit for Cloud and SaaS Architectures
- VPN is network-centric
- SaaS is application-centric
Result:
- Complex routing
- Inconsistent security policies
- Fragmented access control
4. The Core Design Philosophy of Zero Trust
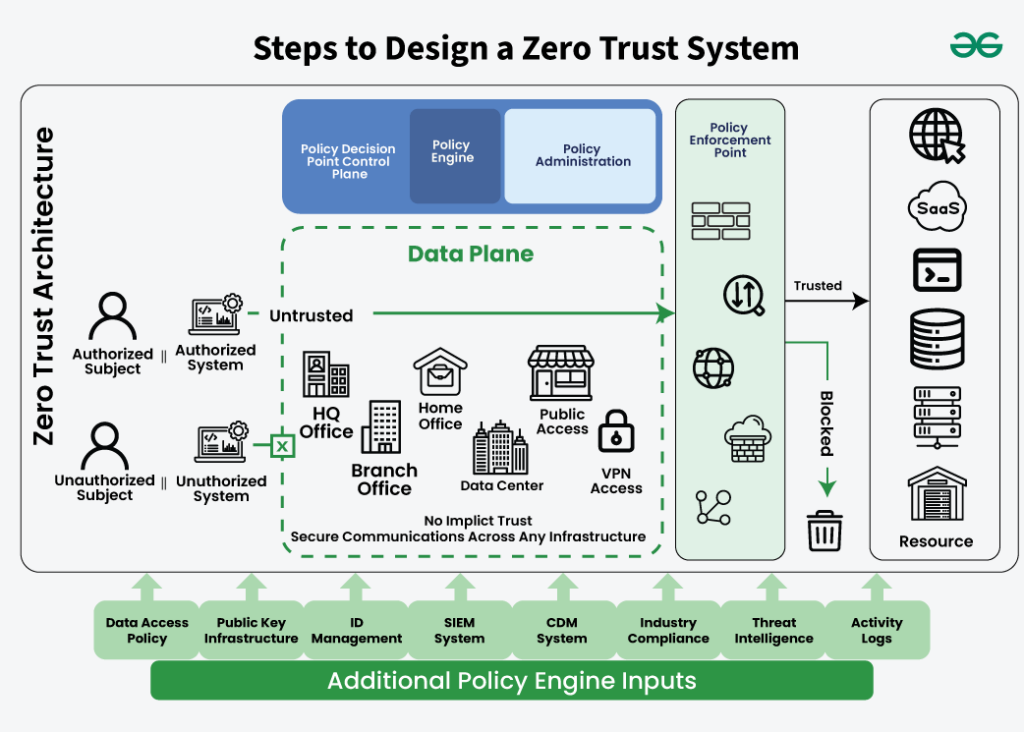
Zero Trust Access Model
User / Device
│
▼
Identity + Device Verification
│
▼
Policy Enforcement Point (Proxy / Gateway)
│
▼
Specific Application or API
Zero Trust assumes:
Never trust based on location.
Always verify based on identity, context, and policy.
5. What Zero Trust Actually Trusts
Zero Trust evaluates:
- User identity
- Device posture
- Certificates (Internal PKI / mTLS)
- Access context
- Real-time risk signals
And it does so:
For every request—not just at login time.
6. Key Differences: Zero Trust vs VPN
| Dimension | VPN | Zero Trust |
|---|---|---|
| Core question | How to enter the network | Can this action be performed |
| Trust basis | Network location | Identity + verification |
| Authentication | One-time | Continuous |
| Lateral movement | Easy | Strongly limited |
| Access scope | Broad | Minimal |
| Cloud / SaaS fit | Poor | Native |
| Architectural focus | Network | Application |
7. Zero Trust Does NOT Mean “No More VPN”
This is a critical clarification.
VPN Still Makes Sense For:
- Network device management
- Non-HTTP legacy systems
- Emergency maintenance access
- Highly specialized admin workflows
👉 VPN is not obsolete—it is often misused.
Where Zero Trust Excels:
- Internal web applications
- APIs and microservices
- ERP / CRM / EIP systems
- SaaS and cloud platforms
8. A Practical Enterprise Evolution Path
Phase 1: VPN (Past)
- Solve basic connectivity
- Limited security guarantees
Phase 2: VPN + Reverse Proxy
- Centralize entry points
- Reduce direct internal exposure
Phase 3: Zero Trust (Present & Future)
- Application-level access control
- HTTPS + Internal PKI
- mTLS and device identity
- Least-privilege enforcement
9. Why Zero Trust Is a Mindset Shift—Not a Product Swap
Many organizations ask:
“Which Zero Trust product should we buy?”
The better question is:
Are we still assuming that internal networks are inherently trusted?
Zero Trust is about:
- Architecture
- Trust models
- Access policies
—not a single appliance or subscription.
10. One-Sentence Summary for Executives
VPN is a tunnel into the network.
Zero Trust is a series of locked doors—each opened only when justified.
In modern enterprises:
- VPN solves connectivity
- Zero Trust solves trust
Conclusion: Not Either–Or, but Right Tool for the Right Job
A mature enterprise strategy is not:
“Eliminate VPN entirely.”
It is:
Stop using VPN as the sole security boundary.
If your organization already uses:
- Reverse proxies
- HTTPS with Internal PKI
- mTLS or strong identity controls
Then you are already on the Zero Trust path.