Why “Being Inside the Network” No Longer Means Being Safe
For decades, enterprises operated under a deeply ingrained assumption:
“If it’s inside the internal network, it must be secure.”
That assumption used to work.
Today, it has become one of the most dangerous security myths in modern enterprise IT.
Zero Trust did not emerge because vendors wanted to sell new products.
It emerged because:
The internal network is no longer a real security boundary.
1. What Is the “Internal Network Security Myth”?
The Traditional Internal Network Model
Internet
│
▼
Firewall / VPN
│
▼
Internal Network (Trusted)
│
▼
All Internal Systems
The core belief behind this model:
Once traffic passes the firewall or VPN, it can be trusted.
Why This Model No Longer Works
Modern enterprises are no longer:
- One office
- One data center
- One subnet
The assumptions behind “internal trust” have collapsed.
2. Why the Internal Network Is No Longer Safe
1️⃣ VPN Turns Attackers into “Legitimate Internal Users”
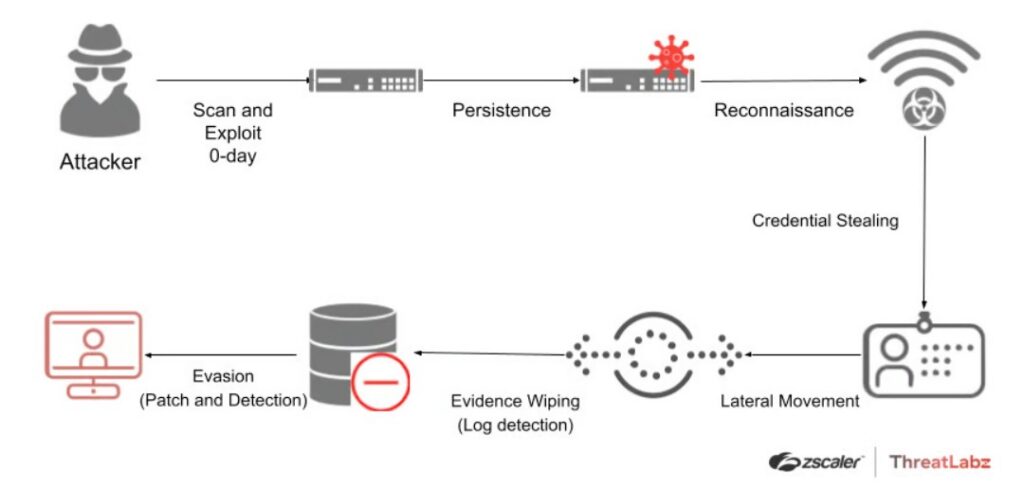
Common realities:
- VPN credentials are phished
- Endpoints are compromised
- Contractors and third parties gain access
Once a VPN connection succeeds:
The attacker doesn’t “break in” — they log in.
2️⃣ The Network Boundary Is Now Blurred or Invisible
- Docker and Kubernetes
- Hybrid and multi-cloud deployments
- SaaS mixed with on-prem systems
A simple but uncomfortable question:
Where exactly is your “internal network” today?
3️⃣ Lateral Movement Inside the Network Is Too Easy
In many internal environments:
- Systems implicitly trust each other
- Network reachability equals authorization
The result:
- One compromised system
- Rapid lateral movement
- Widespread internal exposure
3. Common Internal Network Security Myths
❌ Myth 1: Firewalls Are Enough
Firewalls control:
- Which IPs can connect
They do not control:
- Who you are
- What you are allowed to do
❌ Myth 2: VPN Is a Security Control
VPN solves:
- Connectivity
It does not solve:
- Authorization
- Ongoing verification
❌ Myth 3: Internal Systems Don’t Need Strong Authentication
“Only internal users access it” is exactly why:
Attackers love internal systems.
❌ Myth 4: Internal Traffic Doesn’t Need Encryption or Verification
In a Zero Trust world:
Encryption without identity verification is not security.
4. How Zero Trust Directly Rejects the Internal Network Myth
The very first assumption of Zero Trust is:
The internal network is untrusted by default.
This is not pessimism — it is realism.
5. The Zero Trust Access Model
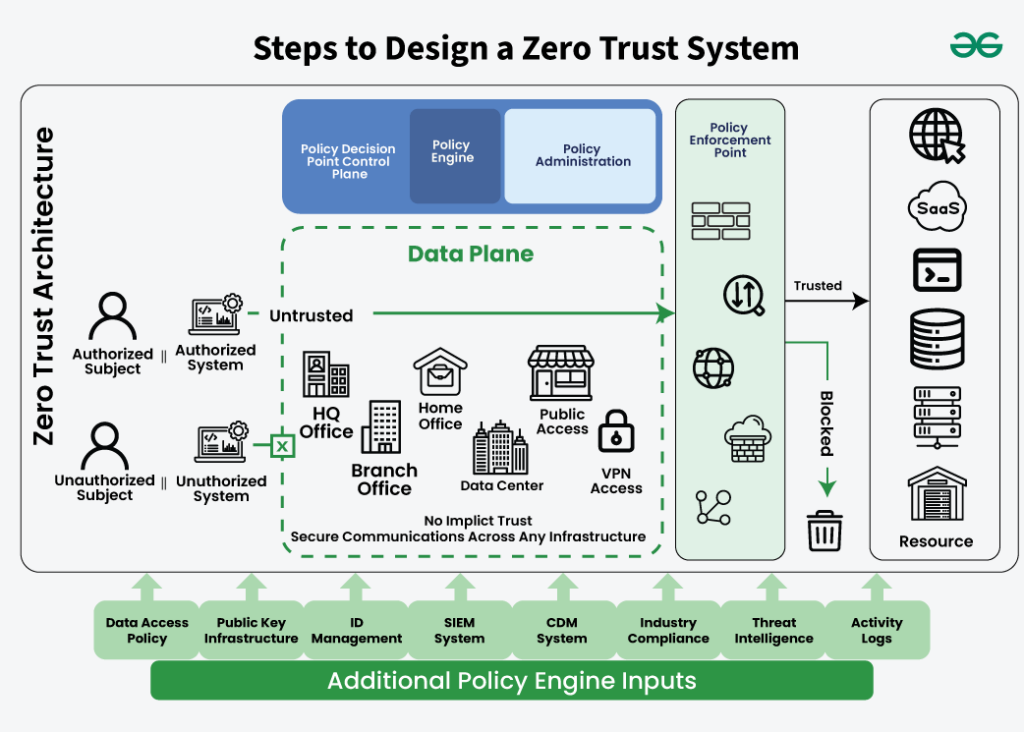
User / Service
│
▼
Identity + Context Verification
│
▼
Policy Enforcement Point
│
▼
Specific Application
6. Zero Trust Cares About “Who You Are,” Not “Where You Are”
Zero Trust does not ask:
Are you inside the network?
It asks:
- Who are you?
- Is your device trusted?
- Are you allowed to perform this specific action?
- Why now?
And it asks these questions:
For every single request.
7. How Zero Trust Dismantles Internal Network Myths
| Internal Network Myth | Zero Trust Reality |
|---|---|
| Inside = trusted | No implicit trust |
| Firewall is the boundary | Boundary moves to the application |
| VPN equals security | VPN ≠ authorization |
| Internal access needs less verification | Every request is verified |
| Internal traffic doesn’t need protection | Encryption + identity required |
8. Zero Trust Does NOT Mean “Trust Nothing”
A common misunderstanding.
Zero Trust actually means:
Trust must be explicit, verifiable, and revocable.
Not:
- Implicit
- Permanent
- Based on network location
9. Practical Enterprise Steps to Break the Myth
Step 1: Stop Treating VPN as a Security Boundary
- VPN is a transport mechanism
- Internal systems should not open up simply because VPN is connected
Step 2: Centralize Access Through Reverse Proxies
- All internal web apps and APIs
- Single enforcement point
- Identity-based access control
Step 3: Enforce Verified Encryption Internally
- HTTPS everywhere
- Internal PKI
- Proxy → Backend certificate verification
- Prepare for mTLS
Step 4: Apply Least Privilege at the Application Level
- Not “can you access the system”
- But “can you perform this operation”
10. One Sentence Every Enterprise Should Remember
The internal network is not a safe zone — it is where attackers want to stay.
Zero Trust is not a future trend.
It is a response to present-day reality.
Conclusion: Zero Trust Doesn’t Destroy the Internal Network — It Makes It Honest
Zero Trust does not demand:
- Immediate replacement of all infrastructure
- A full redesign overnight
It asks only one thing:
Acknowledge that “internal” does not equal “secure,”
and let security be built on verification instead of assumptions.
The moment an enterprise accepts this,
it has already begun its Zero Trust journey.