The Incident That Separates Mature PKI from Fragile PKI
Once an enterprise deploys an Internal PKI, one uncomfortable question will eventually surface:
“What happens if our CA is compromised?”
The more realistic and dangerous version of that question is:
“What if our Intermediate CA private key is compromised?”
This is not a hypothetical exercise.
It is a high-impact, inevitable risk scenario for any organization operating its own PKI.
This article walks through a realistic incident drill, step by step, showing:
How an enterprise survives an Intermediate CA compromise — or fails.
1. The Most Important Conclusion (Read This First)
Intermediate CA compromise ≠ total PKI collapse
IF — and only if — your PKI was designed correctly.
If it was not, the result is usually:
- Complete loss of trust
- Mass service outages
- Emergency PKI rebuild
2. Why the Intermediate CA Is the Most Likely Failure Point
Standard Enterprise PKI Hierarchy
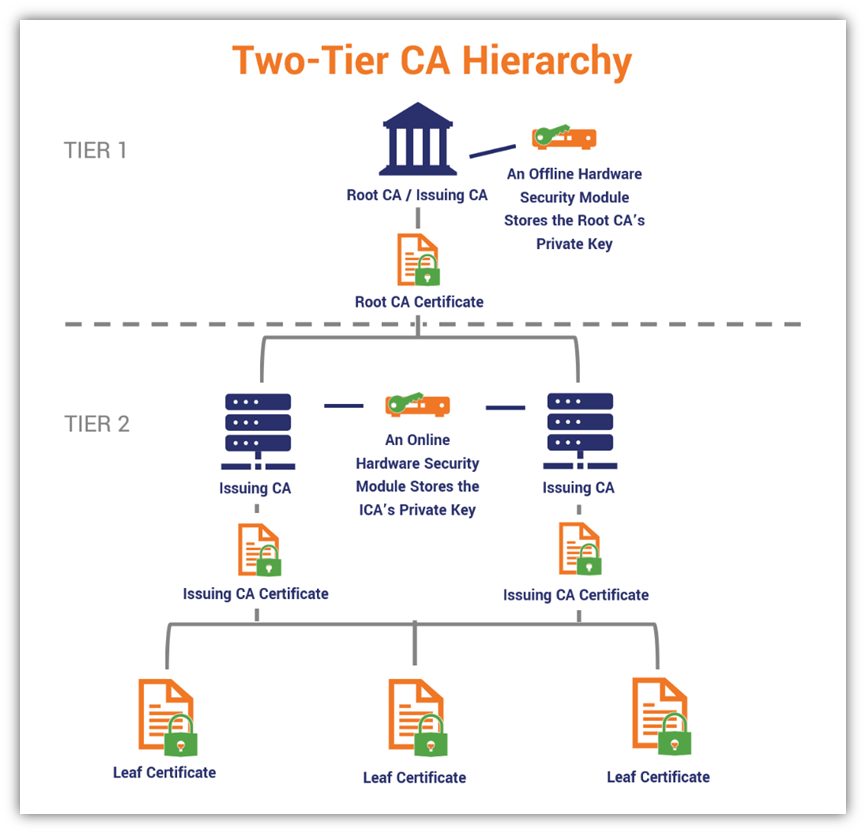
Root CA (Offline)
│
▼
Intermediate CA (Online)
│
▼
Server / Client Certificates
Roles and Risk Levels
| CA Type | Characteristics | Risk |
|---|---|---|
| Root CA | Offline, rarely used | Very low |
| Intermediate CA | Online, signs certificates | Highest |
👉 The vast majority of real-world PKI incidents involve Intermediate CAs.
3. Incident Scenario (Drill Assumptions)
Assume the following:
- Possible leakage of an Intermediate CA private key
- Time of compromise is unknown
- Many server and client certificates already issued
- mTLS, proxies, and internal services depend on this CA
At this moment, technical skill matters less than decision order.
4. Step 1: Classify the Incident Correctly
Intermediate CA private key compromise = P0 / Critical Security Incident
Why?
- Attackers can mint valid certificates
- mTLS identity guarantees collapse
- Zero Trust trust chains are broken
👉 This is not a “monitor and observe” situation.
5. Step 2: Immediately Freeze the Compromised CA
Immediate Actions
- ❌ Stop issuing certificates from this Intermediate CA
- ❌ Disable all automated issuance (ACME, APIs)
- ❌ Lock down CA systems and access paths
👉 Never “just issue one more cert” to buy time.
6. Step 3: Create a New Intermediate CA (Not a New Root)
Correct Recovery Strategy
- Keep the Root CA unchanged
- Use the Root CA to sign:
Intermediate CA v2
This step only works if:
Your Root CA is truly offline and uncompromised
7. Step 4: Full Certificate Rotation (There Is No Shortcut)
Impact Scope
| Certificate Type | Rotation Required |
|---|---|
| Server Certificates | ✅ Mandatory |
| Client Certificates (mTLS) | ✅ Mandatory |
| Trust Stores | ✅ Mandatory |
| CRL / OCSP | ⚠️ Update required |
👉 There is no “partial” safe recovery.
8. Step 5: Trust Chain Transition Without Service Outage
Recommended Strategy: Dual-CA Transition
During a controlled transition window:
- Systems trust both:
- Old Intermediate CA
- New Intermediate CA
- Services gradually deploy new certificates
- Old trust is removed only after full migration
👉 This step determines whether the business stays online.
9. Step 6: Decommission the Compromised Intermediate CA
Once migration completes:
- Mark the old Intermediate CA as Compromised
- Publish CRLs / update OCSP
- Remove it from all trust stores
- Finalize incident documentation
10. What If the Root CA Is Compromised?
That is a different universe.
Root CA compromise means:
- Entire trust anchor is invalid
- All certificates become untrustworthy
- PKI must be rebuilt from scratch
👉 This is why Root CAs must remain offline.
11. What This Incident Drill Actually Tests
This drill is not testing cryptography.
It is testing whether:
- CA hierarchy is properly layered
- Root CA is truly offline
- Certificates can be rotated quickly
- Trust stores can be updated safely
- Teams know what to do before panic begins
12. Common Fatal Enterprise Mistakes
| Mistake | Consequence |
|---|---|
| Root and Intermediate CA mixed | Total PKI collapse |
| No fast re-issuance capability | Prolonged outage |
| Unmanageable certificate lifecycle | mTLS failure |
| No prior drill | Chaos during real incident |
13. One Sentence Every Enterprise Should Remember
PKI does not fail because incidents happen —
it fails because no one planned for them.
An Intermediate CA compromise is survivable.
Being unprepared is not.
Conclusion: PKI Maturity Is Proven in Failure, Not Success
A mature enterprise PKI is not defined by:
- “We’ve never had an incident”
It is defined by:
“When an incident happens, we have a path, a process, and time.”
If your organization already uses:
- Internal PKI
- mTLS
- Zero Trust architectures
Then this incident drill is not optional —
it is required to prove your PKI is real, not theoretical.