From Verifiable Certificates to Unspoofable Service Identity
After an enterprise has completed the following steps:
- Built an Internal CA / PKI
- Enforced HTTPS across internal systems
- Correctly enabled TLS verification on reverse proxies
The next inevitable question becomes:
“How do we actually use our Internal CA in an mTLS architecture?”
Many enterprises stall at this stage—not because the technology is unavailable, but because:
- The responsibilities of Internal CA vs mTLS are unclear
- Teams don’t know which connections truly need mTLS
- There is fear of certificate lifecycle chaos
This article provides a hands-on, enterprise-oriented guide to designing and operating an
Internal CA + mTLS architecture that is correct, stable, and sustainable.
1. Clarifying Roles: Internal CA vs mTLS
Role of the Internal CA
- Issues certificates
- Establishes trust roots
- Provides verifiable identity sources
👉 Internal CA is the foundation of trust — not the security policy itself
Role of mTLS
- Performs mutual identity verification
- Ensures both sides of a connection are who they claim to be
👉 mTLS is how trust is enforced and used
One Critical Sentence
Internal CA defines who can be trusted.
mTLS proves the connection endpoints are truly that identity.
2. Typical Enterprise Internal CA + mTLS Architecture

Internal CA
├─ Server Certificates
├─ Client Certificates
└─ Trust Chain
Service / Client
│ (Client Certificate)
▼
Reverse Proxy / Gateway
│ (Server + Client Certificate)
▼
Backend Service
The goal is not mTLS everywhere, but rather:
Each mTLS connection exists for a clear, risk-driven reason.
3. Internal CA Design Principles for mTLS
1️⃣ Certificate Purposes Must Be Strictly Separated
| Certificate Type | Purpose |
|---|---|
| Server Certificate | Represents a service |
| Client Certificate | Represents a caller |
| CA Certificate | Trust anchor |
❌ Never reuse certificates across roles
👉 Mixing roles breaks the mTLS trust model
2️⃣ Client Certificates Are the Core of mTLS
Despite the perceived complexity of mTLS:
80% of mTLS success depends on proper client certificate design.
Poor client certificate practices guarantee failure.
3️⃣ Recommended Client Certificate Attributes
- SAN:
- Service name
- Environment (prod / staging)
- Extended Key Usage:
- Client Authentication
- Validity:
- 90 days to 1 year
4. The Best Starting Point: Reverse Proxy → Backend mTLS
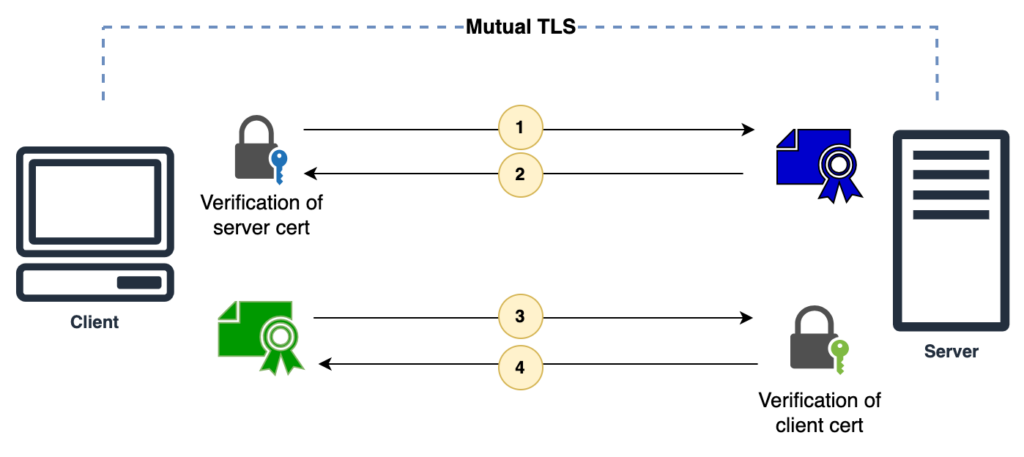
Why This Is the Ideal First Step
- Limited number of connections
- Centralized enforcement
- Easy rollback
Practical Model
- Backend services require client certificates
- Reverse proxy presents a client certificate
- Backend trusts only the required Internal CA
👉 This single step blocks a large class of lateral movement attacks
5. Service-to-Service mTLS (Second Phase)
Service A (Client Certificate)
│ mTLS
▼
Service B (Server Certificate)
Suitable Scenarios
- API platforms
- Microservices architectures
- Internal system integrations
Practical Rules
- One service = one client certificate
- Certificates are identities
- IP addresses and network location are no longer trusted
6. Trust Boundary Design with Internal CA
❌ Common Enterprise Mistakes
- All systems trust the same CA indiscriminately
- All client certificates are treated equally
✅ Correct Approach
- Split CAs by purpose (or at least logically isolate them)
- Backend services trust only the CA they need
- Services and proxies hold only required certificates
👉 Trust must always be minimized
7. Certificate Lifecycle Management (The Survival Factor)
The most common reason mTLS fails in enterprises is not security:
It is certificate expiration combined with operational fear.
Mandatory Capabilities
- Certificate expiration monitoring
- Clear renewal workflows
- Certificate revocation without service-wide outages
8. Common mTLS Pitfalls to Avoid
| Pitfall | Outcome |
|---|---|
| Enabling mTLS everywhere | Large-scale outages |
| Mixing client and server certs | Broken trust model |
| No expiration monitoring | Unexpected downtime |
| No rollback strategy | Verification gets disabled |
| Using mTLS as ACL | Architectural misuse |
9. Internal CA + mTLS in Zero Trust Architecture
Zero Trust is built on:
Identity, verification, and least trust
mTLS provides:
- Cryptographically strong service identity
- Trust independent of network location
👉 In enterprise environments:
mTLS is one of the strongest implementations of service identity in Zero Trust systems
10. One-Sentence Enterprise Recommendation
Don’t aim for “mTLS everywhere.”
Aim for “mTLS where identity must not be spoofed.”
Start with:
- Reverse proxy → backend
- Critical APIs
- High-risk internal systems
That alone delivers significant security value.
Conclusion: mTLS Succeeds Through Restraint, Not Aggression
The goal of Internal CA + mTLS is not to build an
overly complex, fragile security system.
The real goal is:
To provide unspoofable identity where it matters most.
If your enterprise already has:
- An Internal CA
- Correct TLS verification
- Clearly defined trust boundaries
Then mTLS becomes a natural evolution, not a painful transformation.