HTTPS Without Identity Verification Is Not Secure
In many enterprise environments, you will eventually encounter configurations like these:
- Apache
SSLProxyVerify none - Nginx
proxy_ssl_verify off; - Java
TrustAllCertificates - curl
curl -k https://internal.service
The justification is almost always the same:
“It’s internal. We’ll disable verification for now.”
But the reality is far more serious:
Disabling SSL verification is one of the most common and dangerous security landmines in enterprise systems.
This article explains why this is not a harmless shortcut, but a systemic security failure—from both an operational and attacker’s perspective.
1. The Fatal Misunderstanding: HTTPS ≠ Verification
Many people assume:
If it’s HTTPS, it’s secure.
But TLS / HTTPS provides two completely different functions:
- Encryption – protects data in transit
- Authentication – verifies who you are talking to
What Disabling SSL Verification Actually Means
✔ Traffic is encrypted
❌ You have no idea who the other party is
That is equivalent to:
Having an encrypted conversation with an unknown identity.
2. Attackers Love It When You Disable Verification
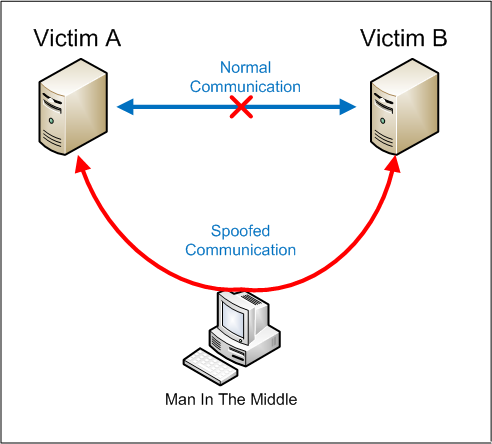
A Very Real Attack Scenario
- Attacker gains internal access (phishing, leaked VPN credentials, weak passwords)
- Attacker impersonates a backend service
- Reverse proxy or application accepts the connection because SSL verification is disabled
- Attacker can:
- Steal credentials
- Inject malicious responses
- Modify or corrupt data
- Move laterally inside the network
👉 TLS encryption does nothing to stop this attack.
3. Why Enterprises Are Especially Vulnerable
1️⃣ Poorly Designed Internal CA / PKI
- Self-signed certificates everywhere
- Broken CA chains
- SAN / SNI mismatches
👉 The fastest “fix”? Disable verification.
2️⃣ Dangerous Defaults in Proxies and SDKs
- Nginx does not verify backend certificates by default
- Some SDKs silently trust all certificates
- Docker images copy entire CA bundles without review
👉 Many failures are silent and invisible.
3️⃣ “Temporary” Disabling That Becomes Permanent
- Dev: disabled “just for testing”
- Test: postponed
- Prod: nobody dares to touch it
👉 This is one of the most common real-world outcomes.
4. The Real Consequences of Disabling SSL Verification
❌ 1. MITM Attacks Become Undetectable
- You cannot distinguish:
- A legitimate service
- A fake or malicious service
❌ 2. Zero Trust Architecture Completely Breaks
Zero Trust is built on one core principle:
Every connection must verify identity
Disabling SSL verification means:
- You only have encryption
- You have no trust validation
👉 This directly violates Zero Trust principles.
❌ 3. Incident Responsibility Becomes Unclear
When something goes wrong:
- Was the certificate compromised?
- Was the service spoofed?
- Was DNS poisoned?
👉 Because verification was disabled, there is no trust boundary to analyze.
❌ 4. Security Audits Will Fail Immediately
- ISO 27001
- SOC 2
- Financial regulations
- Public company security guidelines
👉 Disabled SSL verification is an automatic audit failure.
5. The Right Question Is Not “On or Off”
The real question is not:
Should we verify certificates?
The real question is:
Who should we trust, and how far should that trust extend?
6. The Correct Enterprise Solution (Practical)
1️⃣ Build a Real Internal PKI
- Offline Root CA
- Operational Intermediate CA
- Purpose-separated certificates
👉 Make verification possible, not painful.
2️⃣ Enforce Verification at the Proxy Layer
Apache (Example)
SSLProxyVerify require
SSLProxyCheckPeerName on
SSLProxyCheckPeerExpire on
Nginx (Example)
proxy_ssl_verify on;
proxy_ssl_trusted_certificate /etc/nginx/internal-ca.pem;
proxy_ssl_server_name on;
3️⃣ Minimize Trust Scope
- Do not trust all Root CAs
- Proxies trust only required CAs
- Backend certificates contain only necessary SANs
4️⃣ Treat “Disabling Verification” as an Incident
If verification must be disabled temporarily:
- Time limit
- Tracking record
- Explicit rollback plan
👉 Otherwise, it becomes security debt.
7. The Only Scenario Where Disabling Verification Is Acceptable
There is exactly one:
Fully isolated, short-lived, non-production debugging
And only if:
- No real data
- No external connectivity
- Clear re-enablement plan
👉 Production environments have no excuse.
8. One-Sentence Enterprise Security Summary
Disabling SSL verification does not “reduce security”—it abandons identity verification entirely.
In modern enterprise architectures:
- Internal ≠ trusted
- HTTPS ≠ verified
- Encryption ≠ identity
True security requires:
Encryption + Verification + Minimal Trust
Conclusion: This Is a Landmine You Only Need to Step on Once
Most enterprises are not breached by advanced attacks.
They are breached by:
- One
verify off - One “temporary” workaround
- One assumption that internal networks are safe
After an incident, this configuration line will always be found.
If you are building:
- Reverse proxy architectures
- Internal PKI
- Zero Trust security models
There is only one correct conclusion:
Never disable SSL verification.
Fix certificate problems—do not bypass them.