The Most “Legitimate” Way for Attackers to Move Inside Your Network
When enterprises review major security incidents, one uncomfortable pattern appears again and again:
Attackers didn’t break into the internal network — they logged in.
And in a large percentage of cases, that “login” happened through a VPN.
This article explains a critical but often misunderstood reality:
VPN is not a vulnerability by itself —
but it is frequently the most effective starting point for lateral movement.
1. What Is Lateral Movement?
Lateral movement refers to the phase of an attack where:
An attacker, after gaining initial access, moves sideways inside the environment to compromise additional systems, accounts, and privileges.
A typical attack chain looks like this:
- Initial access
- Foothold establishment
- Lateral movement
- Privilege escalation
- Impact expansion
👉 VPN commonly sits at the intersection of Step 1 and Step 2.
2. VPN’s Trust Model Favors Initial Access
Traditional VPN Access Model
User
│ VPN Authentication
▼
Internal Network (Trusted)
│
▼
Multiple Internal Systems
The core assumption behind VPN:
If authentication succeeds, the user is now part of the trusted internal network.
That assumption is convenient for employees —
and extremely convenient for attackers.
3. Why VPN Is an Ideal Lateral Movement Entry Point
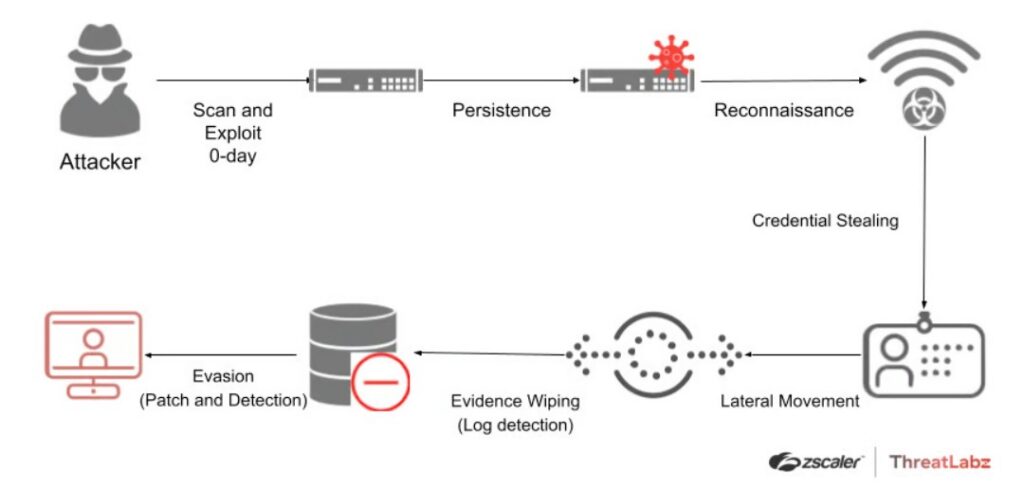
1️⃣ VPN Credentials Are Easy to Obtain
Common sources include:
- Phishing emails
- Malware-infected endpoints
- Reused passwords
- Contractor or third-party accounts
Once VPN credentials are compromised:
Attackers gain legitimate access, not an exploit path.
2️⃣ VPN Authentication Is Usually One-Time
- Authentication happens at login
- Trust persists for the entire session
The result:
Trust is granted once — and lasts far too long.
3️⃣ VPN Access Often Means Overexposed Internal Networks
In many enterprises:
- Network reachability implies authorization
- Internal scanning is unrestricted
- Systems trust “anything on the subnet”
👉 VPN access frequently unlocks far more than intended.
4. VPN and Lateral Movement: A Perfect Combination
From an attacker’s perspective:
| VPN Capability | Attacker Benefit |
|---|---|
| Stable encrypted tunnel | Long-term persistence |
| Internal IP address | Appears as legitimate user |
| Network reachability | Easy scanning and probing |
| Encrypted traffic | Harder detection |
👉 VPN doesn’t just let attackers in — it helps them blend in.
5. Why Enterprises Detect Attacks Too Late
From the system’s point of view:
- VPN login is valid
- Internal traffic looks normal
- Lateral scans resemble admin activity
Security tools often see “internal behavior,” not “external intrusion.”
This delays detection until damage is already done.
6. VPN Is Not the Problem — Over-Trust Is
This distinction is critical:
VPN itself is not a vulnerability.
The real issue is:
- Treating VPN as a security boundary
- Equating “VPN connected” with “fully trusted”
That assumption is exactly what enables lateral movement.
7. How Zero Trust Breaks the Lateral Movement Chain
Zero Trust’s First Principle
The internal network is not trusted — and VPN does not equal authorization.
Zero Trust Controls That Matter
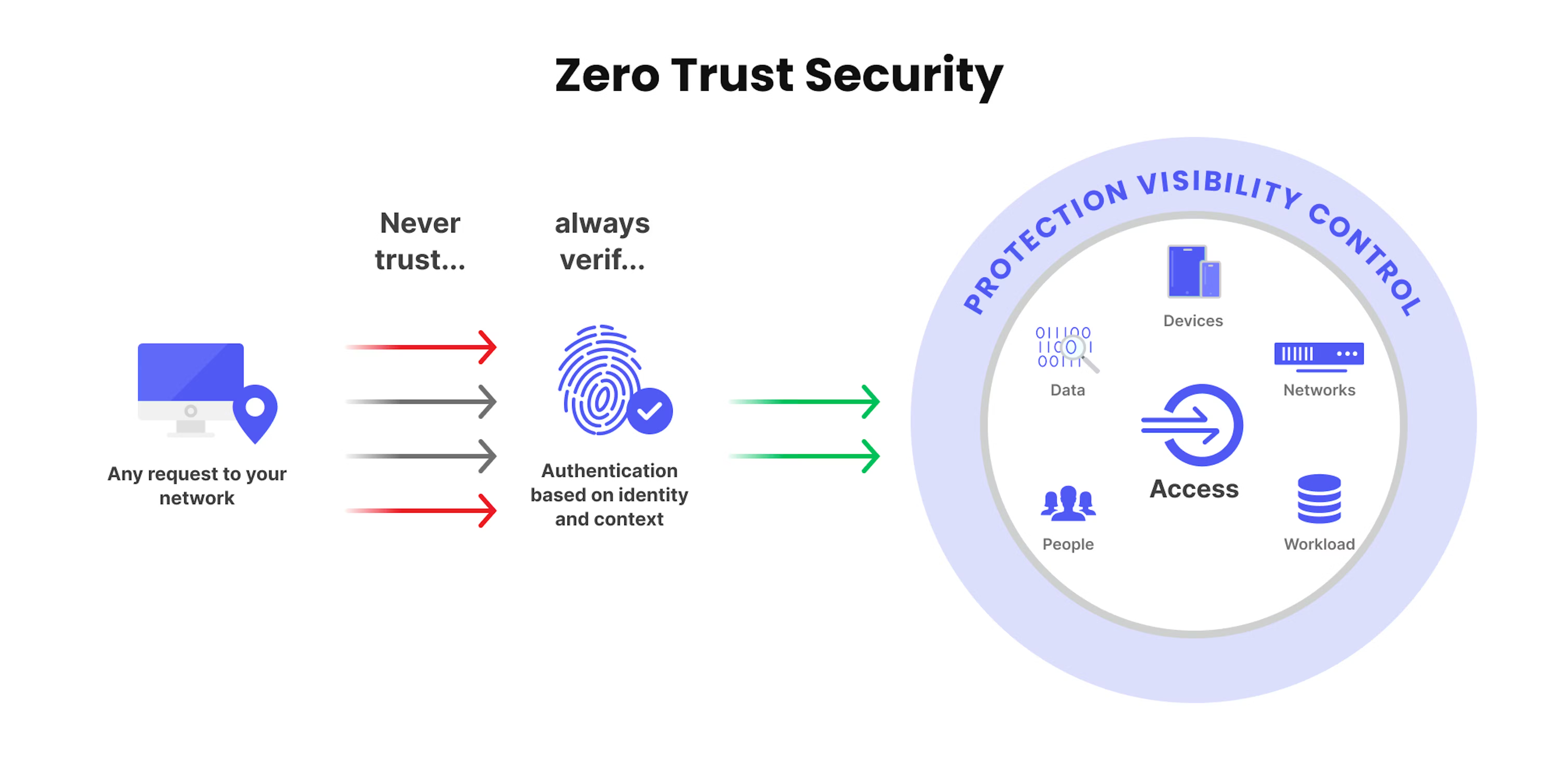
- Continuous verification
- Identity-based access (not network-based)
- Application-level authorization
- Least privilege enforcement
- mTLS and service identity
Impact on Attackers
Even if attackers:
- Successfully connect via VPN
They still:
- Cannot enumerate systems
- Cannot freely move laterally
- Are constrained to minimal access
👉 The attack is contained instead of spreading.
8. Practical Steps to Reduce VPN Lateral Movement Risk
1️⃣ Stop Treating VPN as the Only Entry Point
- Route internal web apps and APIs through reverse proxies
- Centralize identity and policy enforcement
2️⃣ VPN Should Not Mean “Full Network Visibility”
- Limit reachable resources
- Apply segmentation even after VPN login
3️⃣ Enforce Identity Inside the Network
- HTTPS everywhere
- Internal PKI
- Proxy → Backend certificate verification
- Prepare for mTLS adoption
4️⃣ Move from One-Time Trust to Continuous Verification
- Device posture checks
- Certificate-based identity
- Behavioral monitoring
9. One Sentence Every Enterprise Should Remember
VPN is not dangerous —
but using VPN as a trust boundary makes lateral movement inevitable.
Conclusion: Attackers Don’t Fear VPN — They Fear Losing Implicit Trust
In modern enterprises:
- VPN still has valid use cases
- But it must no longer represent “full internal trust”
When organizations ensure that:
- VPN is just a transport layer
- Authorization happens at the application layer
- Verification is continuous
Then:
Lateral movement becomes difficult, expensive, and visible.